The world has been under attack since 12th May 2017. A ransomware attack that started hitting developed countries from Europe, to America and spread through to Asia, India, Japan and China, has heighted the debate over cybercrime, internet regulation and cybersecurity readiness. The WannaCry, a short for WannaCrypt ransomware, has locked thousands of computers in more than 150 countries. Users are confronted with a screen demanding a US $300 payment to restore their files.
Because the only patch for human stupidity is on-going awareness training, and the fact that most people are lazy at not only attending and concentrating during training, they rarely apply the skills learnt, Crypto locker has hit gold. Thanks to the 2009 innovation of digital currency, Bitcoin, affected users are required to pay a ransom using Bitcoins. It is so convenience person to person, mode of payment that is so good as it is 100% decentralized – meaning that there is no financial institution involved and the payment, once made, cannot be cancelled.
The challenge with today’s innovation is keeping the taxpayer as a toothless spectator. So far no solution by tax authorities to collect revenues via Bitcoin currency. Users are anonymous. So difficult to know exact location. And once an use the Bitcoin revenue to transact online and the cycle continues.
Now back to WannaCry. Like its name. The victim is rendered so helpless that all they can do is want to cry. Simply put, they ‘WannaCry.’Of course crying won’t help unlock your files. And paying is no guarantee you will have the files back.
A case in point.
On Friday 22nd November2013, HPfriday received an email, with an attachment named “Alex”. Given that “Alex” had been a former colleague of HPfriday, he opened the attachment. On opening the attachment, he saw the files on his laptop run through so first, that in a blink of an eye,a message below appeared on the HPfriday laptop:
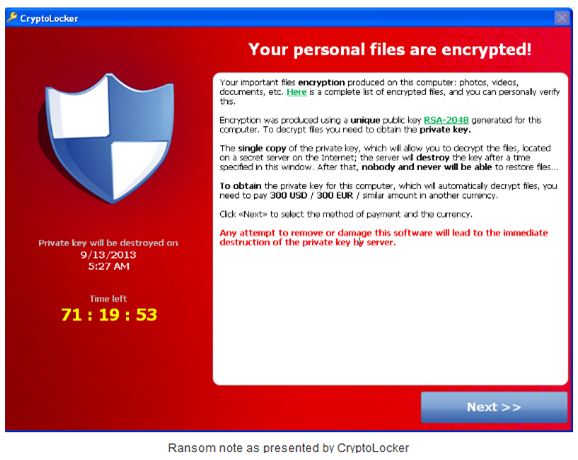
This led to encryption of all the files on HPfriday’s computer (ie desktop, C and D drive). At the end of the day, when synchronization of documents took place, even his documents on the server were encrypted. Because it was beyond belief, HPfriday decided to just first cool off, thinking it is just a joke or the screen would disappear within a few minutes. He closed the laptop lid and went to first attend to other priorities with hope that the problem would just disappear. It did not.
On Tuesday, HPfriday called his IT staff to help remove the above screen from his computer and it’s at that point they noticed that all documents were not opening. He just wanted to cry. I don’t know about you. But if you are a serious executive, lots of your work is on your laptop. Having CryptoLocker visit you could mean days of missed timelines and productivity. And if you a not lucky, miss project milestones and key reporting timelines. It could even lead to serious legal obligations.
In UK, at the National Health Services (NHS), most patient records cannot be accessed. That is how inhuman this WannaCry folks can get. No conscience at all. They don’t want to know their victims. They just need US $300 Bitcoins. If you are lucky that they only ask for that.
The IT staff tried all they could and failed. The matter was escalated to the national body responsible for computer emergencies and they too were helpless.
As experts of last resort, that is how the matter landed on our desk. I was called to respond to the incident with just one simple request “help us recover our critical files.” All files in my documents, we need them.
This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program promises to decrypt the files that it encrypted. This malware can also encrypt files on remote computers within the network.
And this gives us a big pointer. That you must keep backing up your critical files to enable continuity in case of such disruptive incident. You will not just wannacry. You will cry if CrypoLocker finds you before having backed up your data on a daily basis or more frequent depending on the sensitivity of your operations and the volumes of your data. By far remote backup away from your network is critical. The ransomware has been nicknamed “WannaCry” because it causes a lot of inconveniences recovering and restoring data. However, if the victims had not kept live backups, they would have called it “Rivers of Tears.” Don’t launch.
The first responder activities. The internal team had made the following observations
- The computer was removed from the enterprise network and scanned. The Trojan was identified as Trojan-Ransom.win32.Blocker.cmkv
- The documents on the server were restored from a backup up to October 1st 2013. Files accumulated over a two months period had been lost.
- Research was carried out online to identify a decryptor for this Trojan; all the tools we tried could not yield a positive result
Findings by Summit Consulting Ltd
This malware is a cryptolocker ransomware program that was released around the beginning of September 2013. This malware encrypts files using a mixture of RSA & AES encryption.When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 or $300 in order to decrypt the files. This screen will also display a timer stating that you have 96 hours, or 4 days, to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program promises to decrypt the files that it encrypted. This malware can also encrypt files on remote computers within the network. So far millions of computers had been compromised worldwide and there was no fix yet, at the time as it to date. The encryption algorithm is based on RSA 20148 bit key which makes it extremely difficult to crack the password. The advice given to users is to safeguard your Network. All files on the victim hard drive were encrypted.
Solution to the problem
We tirelessly gave our best in terms of developing tools that could do reverse engineering of this malware and were successfully able to recover all HPfriday data files. This malware is very dangerous and could strike again if necessary precautions are not done. We were able to recover the files and handover to the client. Unfortunately, the client had to re-install the operating system and all other essential apps.
Our recommendations were as follows:
- Comprehensive Security Audit of the ICT infrastructure. This is very urgent. Conduct a thorough black box pen test (including an elaborate social engineering) and there after a white box pen test, to assess the vulnerabilities present in your network and practical recommended fixes. Just closing specific points, without having clarity of other services and ports on the network could be like a writing on the water.
- Training of users in system security is critical. This elementary can be organized in a phased approach. All users, starting with those manning critical applications and or connected in a network where such critical applications are hosted is a must.
- ICT team taking training ICT security certification training such as Ethical Hacking and counter measures.
- Ongoing live backup to a remote server is critical.
- Real time DB monitoring
- Disable all admin accounts on non-admin users to reduce the risk of unintentional installation of Trojans and other viruses on user machines which could compromise the entire network
- Properly display user security tips to avoid lapses.
Remember, everyone is responsible for the enterprise security.
Visit www.forensicsinstitute.org to enroll to one of our flagship courses like certified secure computer user, certified ethical hacker or certified network defender and become a trusted expert that the CEO and board don’t want to get out of their eyes.
Be secure. For more information visit www.summitcl.com.